As OT (Operational Technology) networks converge with IT networks, network security is a serious concern. OT systems that used to be air-gapped must still protect network communications without interrupting operations. To protect your industrial networks and critical assets, you need a secure network infrastructure with powerful secure routers to build solid network segmentation. The following four steps show how you can secure your OT networks while ensuring they are resilient to threats and disruption.
Operators who manage their OT network (rather than relying on the IT department) can quickly respond to problems and troubleshoot issues more rapidly. Before you can protect the assets on your OT network, you need to know what is there – and what isn’t. It’s critical that OT operators have complete visibility to everything on their networks – just like IT network administrators do. Make sure everything that should be on your OT network is there. And identify anything that should not be there.
Managing your OT network requires controlling who has access to the network by utilizing network Access Control Lists (ACL) and other authentication mechanisms. In other words, everything on the trusted list is allowed to go through the network, and anything not specified is blocked. An Access Control List filters traffic and allows users to configure customized filter criteria and deny access to specific source or destination IP/MAC addresses. For example, access control lists found in Moxa’s Layer 3 Ethernet switches make it easy to quickly establish filtering rules, manage rule priorities, and view overall settings in the display page.
Also, there are simple mechanisms that OT operators can set up to define which equipment, like a PLC, can be connected to the network by port access control or secure “sticky” MAC address, which dynamically associates the mac-address to the port. Without the sticky option, the mac-address association goes away after a specified period of time.
Equipment and devices running on OT networks cannot be upgraded or replaced like they can on IT networks. Many legacy OT devices remain unpatched and are relatively easy for hackers to exploit. Some of those legacy devices may be running on operating systems as old as Windows 95. If no patch is available from the original equipment vendor, consider putting a virtual patch on a device that goes in front of your legacy devices.
Segmenting OT networks prevent cyber threats from spreading to other parts of the network.
Unlike IT networks that can be segmented by dividing the network into different departments with their own set of permissions, OT networks are basically one big Intranet where everything is connected. This makes OT networks more difficult to segment, but not impossible. There are two ways you can segment an OT network:
Moxa recommends:
Establishing Zones and Conduits:
Network Security Control:
Besides managing and segmenting OT networks, it’s also important that remote connections are secure. Protecting the data that is 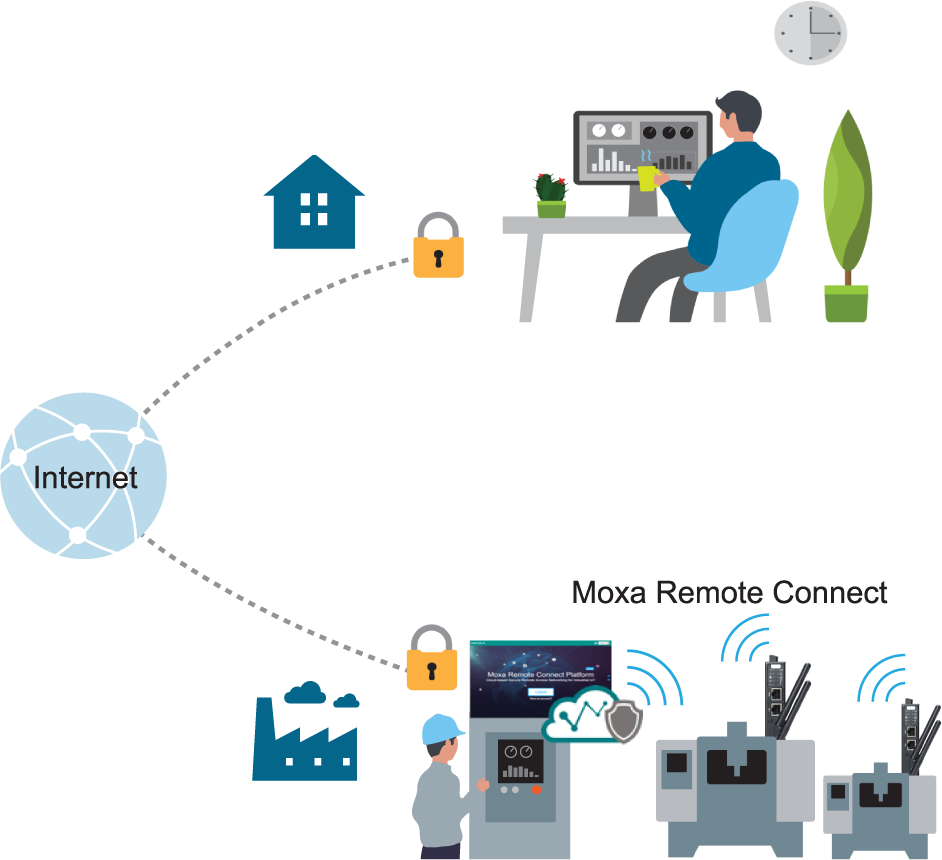 transmitted from your plant or remote site back to the monitoring and control center is absolutely crucial. Ensure that each remote connection to your OT network is both authenticated and encrypted. Authentication verifies the identity of the user requesting access whereas encryption ensures that the data transmitted is securely encoded and cannot be easily deciphered by prying eyes.
transmitted from your plant or remote site back to the monitoring and control center is absolutely crucial. Ensure that each remote connection to your OT network is both authenticated and encrypted. Authentication verifies the identity of the user requesting access whereas encryption ensures that the data transmitted is securely encoded and cannot be easily deciphered by prying eyes.
Moxa’s Remote Connect (MRC) Suite is a management suite for remote connections that lets you easily build remote connections for your devices by using Moxa Remote Connect Quick Link service or you can also build your own private MRC server portal.
As a leading industrial networking provider, MSI TEC can help you develop secure and reliable networking solutions that protect OT environments from cyber threats. As an authorized Moxa, Cisco, Advantech, Axiomtek and Weidmuller distributor, we offer the widest range of rugged networking products that are designed specifically for industrial applications.

Be the first to learn about classes, training, webinars, products news and more.
We use only necessary cookies on this website to provide the best user experience and customer service.