As more OT and IT networks converge, there are several attack surfaces emerging in industrial control systems. Some are known vulnerabilities, but there are also some that are unknown. That’s why it’s important that everyone from management to individual users join forces to support industrial cybersecurity from the edge to the cloud. Here are 5 tips, gathered from industry experts, to help strengthen your cybersecurity journey.
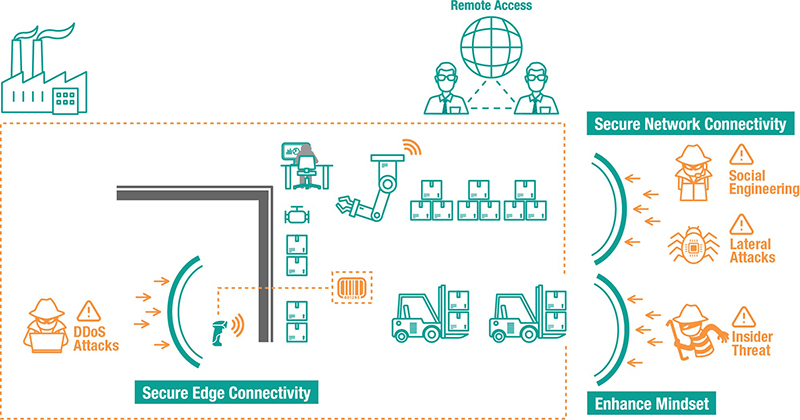
Industrial operations typically include a variety of legacy devices that are vulnerable due to field networks that are no longer air-gapped. Legacy equipment can’t be upgraded quickly and do not have security features embedded into them. To avoid downtime, industrial operations frequently have a mixture of old and new equipment operating together. When this scenario arises, it’s important to have a security-hardened networking device to enable connectivity for legacy devices. In order to ensure that the devices use a secure-by-design methodology, it is advisable to check that the embedded security functions of any networking devices adhere to security standards such as those detailed in the IEC 62443 standard. After confirming this, devices can be set up securely. For instance, we recommend disabling any unused ports and services to minimize available entry points for intruders.
Once the network nodes are configured securely, the next step is to segment the networks following a zone and conduit policy. Dividing the connected networks into segments to enhance network security helps avoid the scenario where the entire network experiences downtime due to a single network node being compromised. It is recommended to have a secured network architecture design, such as network segmentation or a Demilitarized Zone (DMZ), to reduce the risk of threats emerging from the IT network.
It’s also important to choose the right solutions to divide industrial networks into segments. Simply placing an IT firewall in front of the OT network is not sufficient protection for an OT environment. However, this advice is frequently ignored. An IT firewall does not have the capability to recognize industrial protocols, which allows cyber attacks to take place at the supervisory or process level and leaves the system open to vulnerabilities and intruders. Firewalls that are used as solutions in industrial control systems not only segment networks into separated network zones to achieve vertical protection, but should also include the deep packet inspection engine function to filter unauthorized packets without affecting performance of operations and providing horizontal protection.
The purpose of OT/IT network convergence is to collect data and transform it into valuable information. One good option is to utilize cloud technologies, which are convenient to use and have powerful data analysis capabilities, to simplify network convergence. However, when using cloud technologies, remote access poses a significant security concern. Increasingly, machine builders are leveraging cloud platforms to streamline machine maintenance. However, before you are able to reap the benefits, make sure your remote access is secure by using features such as data encryption and a VPN, as this will help keep your critical assets secure.
Once you’ve reduced potential attack surfaces from the edge to the cloud, you need to focus on the people who operate these industrial systems and devices, like outsourced vendors, system integrators, and remote service engineers. Everyone involved in industrial processes must have cybersecurity awareness and know how to leverage these technologies. And they should share the same mindset and attitude to cybersecurity.
According to the security awareness pyramid, cybersecurity can be separated into different awareness stages. Commitment and support from management form the foundations, which is followed by security programs and policies being implemented during the awareness building process. Taking security policies as an example, it is fundamental to define who has Read and Write access based on the security configurations. However, when these policies are rolled out across an entire organization, it becomes a challenge to ensure everyone adheres to them properly. Facility managers often find implementing cybersecurity measures very cumbersome, and subsequently they do not ensure everyone follows the guidelines. Sometimes, they may end up doing things more akin to group level security, instead of ensuring each individual has their own unique log in credentials, and this subsequently opens up new cybersecurity risks.
Once awareness has been established and policies have been defined, employees will pay more attention to their system settings. We understand it can be a complex task to examine all the systems at one time. However, it is never too late to get started. Performing a risk assessment will help define security priorities and from this position it is easier to identify and protect critical assets. A good starting point is to examine configurations. If a large-scale network is being examined, it is recommended to leverage visualization software to check the security settings and adjust the configurations where necessary.
For more security information, visit Moxa’s cyber security microsite.
Click here to contact an MSI TEC network engineer to discuss industrial networking and cybersecurity
Be the first to learn about classes, training, webinars, products news and more.
©2025 MSI TEC, Inc ALL RIGHTS RESERVED
©2025 MSI TEC, Inc ALL RIGHTS RESERVED
We use only necessary cookies on this website to provide the best user experience and customer service.