Integrating IT and OT systems has become a crucial approach for industrial operators aiming to improve operational performance and maintain a competitive edge. However, this convergence also brings heightened cybersecurity challenges, particularly due to the increased use of connected field devices. These systems are especially susceptible to attacks because of outdated hardware, insecure default configurations, legacy communication protocols, and the lack of network segmentation. To mitigate these vulnerabilities and take full advantage of IT/OT convergence, organizations must focus on building strong cyber-resilience. This article explores strategies to improve network security in integrated IT/OT environments.
Governments around the world are responding to the rise in cyber threats against critical infrastructure by introducing stricter cybersecurity regulations. These mandates require industrial companies to adopt security protocols that minimize the impact of cyber incidents. For example, the EU’s NIS2 Directive compels essential service providers to implement cybersecurity practices and report incidents to authorities. Similarly, in the United States, the Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA) obligates critical infrastructure entities to report major cyber events and ransomware payments to the Cybersecurity and Infrastructure Security Agency (CISA). By enhancing their cyber-resilience, industrial operators can confidently integrate IT/OT systems while remaining compliant with these evolving regulations.
Three Key Networking Strategies to Boost Cyber-Resilience
Resilience in business operations relies on the ability to quickly respond to and recover from disruptions, including cyberattacks. Cyber-resilience involves a combination of people, policies, and technologies. From a network design perspective, consider these three strategies to strengthen cybersecurity.
1. Reduce the Attack Surface Across the Network
Minimizing the number of vulnerable points in a network helps organizations recover faster from security incidents and reduces exposure to threats. A well-established method for doing this is the defense-in-depth strategy. This involves choosing secure-by-design devices and implementing multiple layers of network protection. Look for equipment that aligns with industry standards such as IEC 62443 and the NIST Cybersecurity Framework. These standards provide best practices for securing vital infrastructure.
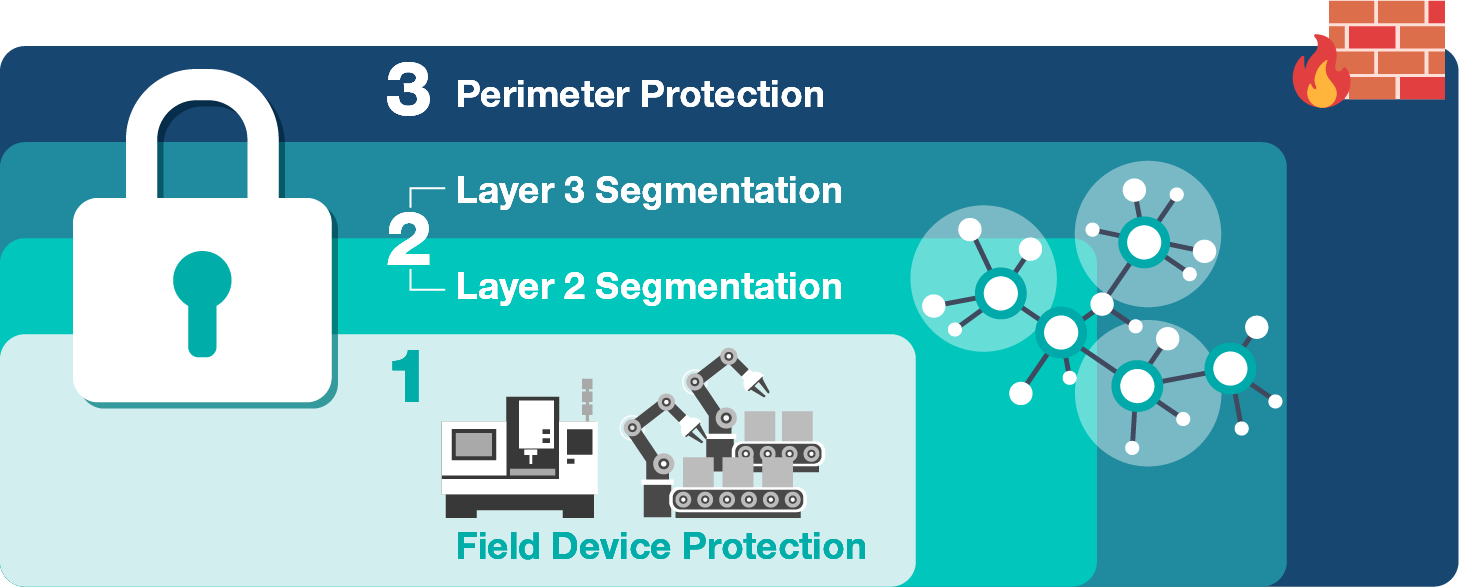
To initiate a multi-layered defense plan, you can follow a straightforward three-part approach:
This three-pronged model creates a solid foundation for layered protection. Depending on your network’s exposure and complexity, additional tools such as secure VPNs can be added. VPNs create encrypted tunnels for remote access, which is especially important when engineers need to access machines from off-site locations.
2. Speed Up Detection of Security Incidents
Even the most robust defenses can be breached, so early detection is critical. Network administrators must have a clear view of all devices and data flows across the network. Use network management systems that can track device status and traffic patterns in real time. These tools alert you to unusual behavior that could indicate an attack.
In addition, consider using intrusion detection systems (IDS) positioned in front of critical systems. IDS tools monitor traffic for signs of abnormal activity and send alerts without disrupting operations. This allows operators to investigate and respond to incidents based on risk, without halting production.
3. Accelerate Recovery After a Cyberattack
Maintaining continuity during an attack is a priority, and rapid recovery is a core element of cyber-resilience. Business continuity is emphasized in the NIS2 Directive, and having a well-developed recovery plan is essential. Start by backing up configuration files for all network devices, so you can quickly restore systems without manual reconfiguration.
Monitoring tools that offer centralized configuration backups, batch firmware updates, and dashboards for security monitoring can greatly simplify the recovery process. Investing in the right tools can reduce downtime and get operations back online much faster.
Build a Stronger Network With Security-Focused Solutions
For industrial organizations to enhance their cybersecurity posture, deploying secure networks is a necessity. However, it is equally important to implement these solutions in a way that does not interfere with current operations. We can help build integrated, secure networking technologies designed to protect industrial systems while maintaining performance and reliability.
Have questions? Contact an MSI TEC network engineer

Be the first to learn about classes, training, webinars, products news and more.
We use only necessary cookies on this website to provide the best user experience and customer service.